Cyber Security Quiz Questions and Answers.
This is the latest freshly curated set of Cyber Security Quiz Questions and answers. End of this post, you can quiz yourself on a flash app with a set of 30 questions.
1. The below logic is an example of what kind of cyber-attack targets the vulnerabilities on the Databases?
‘ OR ‘1’=’1′ — ‘ OR ‘1’=’1′ { ‘ OR ‘1’=’1′ /*
Answer- SQL Injection
Take this Cyber security quiz to test yourself
2. X is a Computer security venture that gives data about security vulnerabilities and helps in penetration testing and IDS signature advancement. Identify X from its logo below.?
![]()
Answer- Metasploit
3. This is a Debian-derived Linux distribution managed and funded by Offensive Security Ltd, designed for digital forensics and penetration testing. Which is this very famous OS majorly developed for Hackers and software testers?
Answers- Kali Linux
4. which OS based on Knoppix was rewritten by Kali Linux?
Answer – BackTrack
5. This is a small piece of code used as the payload in the exploitation of a software vulnerability. It starts the command shell and the attacker can control the machine. Commonly it is written in Machine code. What is this piece of code generally called?
Answer- ShellCode
6. X is an algorithm on a computer system that bypasses security controls. Generally, this is added by the original developer for some legitimate access, which may also be used by a hacker in a malicious way. What is this form of vulnerability called?
Answer- Backdoor
7. If DoS – Denial of Service
What is DDoS?
Answer- Distributed Denial of Service
8. X is a metaphorical name given to a computer connected to the Internet that has been compromised by a hacker, computer virus or trojan horse program and can be used to perform malicious tasks such as sending spam emails, launch DoS attacks of one sort or another under remote direction. What is X?
Answer- Zombie
9. The word X is a combination of the words “robot” and “network”. It is a number of Internet-connected devices, each of which is running one or more bots. This can be used to perform DDoS attacks, steal data, send spam. Identify the word X?
Answer- BotNet
10. _______ networks use simple, low bandwidth communication methods, making them widely used to host botnets. They can be very easily used for coordinating DDoS attacks and spam campaigns. Being able to continually switch channels to avoid being taken down is considered to be the most taken advantage of by this network. FITB?
Answer- IRC
Cyber Security Quiz Questions and Answers
11. X has been defined as “any act that influences a person to take any action that may or may not be in their best interests.”. Basically, it is the psychological manipulation of people into performing actions or divulging confidential information. What is X?
Answer- Social Engineering
12. What is the X mentioning here?
- Email X – where an attacker forges the sending address of an email.
- IP address X – where an attacker alters the source IP address in a network packet to hide their identity.
- Biometric X -where an attacker produces a fake biometric sample to pose as another user
- MAC X – where an attacker modifies the Media Access Control (MAC) address of their network interface to pose as a valid user on a network.
Answer- Spoofing
13. The Tor dark web may be referred to as X, a reference to the network’s TLD suffix .onion and the traffic anonymization technique of onion routing. What is X?
Answer- Onionland
Cyber Security Quiz Questions and Answers 2019
14. If SSL – Secure Socket Layer
What does TLS stand for?
Answer- Transport Layer Security
Cyber Security quiz
15. Identify this organization

Answer- Center for Internet Security
16. Identify this European Security Organisation

Answer- European Union Agency for Network and Information Security
17. _______ was the first personal computer virus?
Answer- Elk Cloner
18. Who is known as the inventor of computer virus defense techniques?
Answer- Fred Cohen
19. What is the name of the program created by Ray Tomlinson to move across the ARPANET and delete the self-replicating Creeper?
Answer- Reaper
20. Identify the logo

Answer- Lulz Security
Cyber Security Quiz
21. What does the acronym VIRUS stand for?
Answer- Vital Information Resource Under Siege
22. According to the worst password list of 2017 and 2018 which one ranks the top?
Answer- 123456
23. Who coined the term Virus?
Answer- Len Adleman
24. Who coined the term worm?
Answer- John Brunner
25. The first virus to infect Windows 95 files is?
Answer- Baza
26. The first virus to infect Java files is?
Answer- Strange BREW
27. The first virus to infect Linux is?
Answer- Staog
28. The first virus which infected command.com is?
Answer- Lehigh Virus
cybersecurity quiz
29. The first major virus which infected the Macintosh computer is?
Answer- MacMag Virus
30. The first virus found in the public domain which spread across Texas through pirated games are?
Answer- Apple Virus 1,2,3
31. The first person to be convicted for writing computer virus code in 1995 is?
Answer- Christopher Pile, for developing Virus toolkit
31. The first web browser to have an integrated a Virus protection system is?
Answer- EPIC Browser
Cyber Security quiz
32. Two Pakistani guys Basit and Amjad wrote a program to protect their medical software from piracy but it turned to be the first IBM PC Compatible virus. What is its name?
Answer- Brain Virus
33. Bob Thomas, working at BBN, wrote a program named X which infected the ARPANET. He later wrote the program Y to destroy X. What are X and Y?
Answer- X- Creeper
Y- Reaper
34. This computer virus came in the form of an email along with a message stating, “Between millions of people around the world I found you. Don’t forget to remember this day every time MY FRIEND. Identify the virus?
Answer- Pikachu Virus
35. X is a malicious computer worm that mainly targets SCADA, PLC systems which were discovered by Sergey Ulasen. What is X?
Answer- Stuxnet
36. Identify this Cyber Security Evangelist

Answer- Eugene Kaspersky
Cyber Security Quiz
37. What was created to sabotage Iran’s nuclear program?
Answer- Stuxnet
38. What is this an example of?
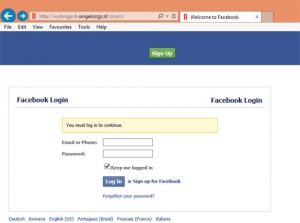
Answer- Phishing
39. This was designed as a replacement for Telnet. It is a cryptographic network protocol for operating network services securely over an unsecured network. What am I talking about?
Answer- SSH(Secure Shell)
40. Norton Antivirus was developed by which company?
Answer- Symantec
41. ___________ is a form of malware that uses social engineering to cause shock, anxiety, or the perception of a threat in order to manipulate users into buying unwanted software. FITB?
Answer- Scareware
42. X was a mass-mailing macro virus, which majorly targeted outlook and word-based systems. What is X?
Answer- Melissa
43. Identify this Computer Security Consultant

Answer- Edward Snowden
44. Identify this logo

Answer- United States Cyber Command (USCYBERCOM)
Cyber Security Quiz
45. What is the famous project by Sunshine Press?
Answer- Wikileaks
46. Identify this computer programmer

Answer- John Mcaffe
47. Identify this logo

Answer- SIGNAL
48. X was designed by the United States National Security Agency, is a cryptographic hash function that takes an input and produces a 160-bit (20-byte) hash value known as a message digest – typically rendered as a hexadecimal number, 40 digits long.
What is X?
Answer- SHA1 Algorithm( Secure Hash Algorithm)
49. ___________ is a widely used hash function producing a 128-bit hash value, designed by Ronald Rivest. FITB?
Answer- MD5 Hashing( Message Digest)
50. Identify this decentralized international hacktivist group

Answer- Anonymous
Now that you’ve completed reading the Cyber Security Quiz Questions and answers. Now complete the Interactive flash quiz now to test how much you’ve learned.
The below logic is an example of what kind of cyber-attack that targets the vulnerabilities on the Databases? 1‘ OR ‘1’=’1′ — ‘ OR ‘1’=’1′ { ‘ OR ‘1’=’1′ /*
Take the above Quiz on Cyber Security for a self-evaluation.
This page of the Cyber Security Quiz will be updated and more questions on Information Security will be added to this Quiz. You can also contribute to this list of Questions. Just mail me at amal@itquiz.in. You’ll get paid 5 Rs/ fresh question. Also, check out the upgrad referral code for joining a degree online.
No payment will be issued for copied Cyber Security Quiz questions. Let me know your comments on the above set of questions.




This was helpful me for a cyber security quiz competition. thank you.
happy to hear that it was helpful for you in a quiz.
Interesting set of quiz questions, and please update more questions like this. Thank you so much
Thanks for the feedback.
Totally loved these set of questions and these quiz was much helpful.
Thanks
I would be participating in an information security quiz next week. Please update more questions on this post.
Thanks for the feedback
Interesting set of questions.
useful questions and very well researched set of Q&A
uber good questions
Can you please post cyber security job interview quiz questions?
the questions are super and helped me on cyber security national level quiz. Thank you admin.
how can i contribute the questions that I created to your website?
cyber tech quiz was awesome
helpful
Really instructive and fantastic body structure of articles,
now that’s user pleasant (:.
Really super